
MS
Static Analysis to the rescue.
Often, the proportion between the number of developers and the number of security auditors within an organization can be up to 100:1. Today, with the help of static analysis tools, software vendors are able to achieve highly secure systems while reducing cost and resources spent on security.
Less is more
The greatest challenge of SAST tools is providing useful data in a usable way. Often a scan yields so many vulnerabilities that the user is overwhelmed and wants to give up working with the system all together.
Recognizing this challenge, Checkmarx developed a tool that visually presents the vulnerable paths, overlapping and combining related events and optimizing the vulnerability remediation process. Users are able to see exactly where the security vulnerability exists and can simulate several scenarios for fix locations at the click of a mouse, before actually fixing the code. This visual screening and data grouping method permits more efficient vulnerability mitigation and enables a single security expert to handle ten times more audit projects.
Translating vulnerabilities to visual paths
Most security vulnerabilities can generally be viewed as input data that is processed by the
system and causes a harmful effect. We often refer to an attack as data that flows from source to the sink. The source is a location where the data is received from an external source, such as a dialog box on a registration form, or a web-service that the system provides. The sink is the last point of the data processing; it can be a command that is performed on the server, a query that is executed on the database or even data that is displayed on another page of the application.
For example, consider a cross-site scripting (XSS) vulnerability. A page that displays data that was received from an external source without validating it, is considered XSS vulnerable because it can be used by an attacker in order to steal user identity (sessions) from the website’s legal users. An attacker exploiting the XSS vulnerability can impersonate and act on behalf of his victims. Ultimately, the cross-site scripting (XSS) vulnerability can be viewed as a path where data travels from the application entry point to another page displayed by the application.
Checkmarx reports
Figure 1: Snapshot of a graph display of ‘insecure data storage’ vulnerabilities that were found in an Android application.
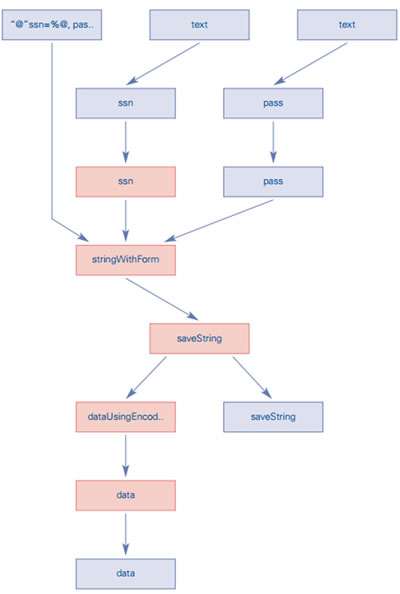
Recognizing this challenge, Checkmarx developed a tool that visually presents the vulnerable paths, overlapping and combining related events and optimizing the vulnerability remediation process.
About Checkmarx
Checkmarx is the developer of next generation Static Code Analysis (SCA) solutions.
The company pioneered the concept of a query language-based solution for identifying technical and logical code vulnerabilities.
Checkmarx provides the best way for organizations to introduce security into their Software Development Lifecycle (SDLC) which systematically eliminates software risk. The product enables developers and auditors to easily scan un-compiled / un-built code in all major coding languages.
Checkmarx was recognized by Gartner as sole visionary in their latest SAST magic quadrant and as Cool vendor in application security. Customers include multiple Fortune 500, government organizations and SMBs.
Contact number: +972-3-7581800
Contact mail: This email address is being protected from spambots. You need JavaScript enabled to view it.






